- Monitor the network traffic in near real-time;
- Dynamic filtering displaying historical traffic results;
-
The dynamic traffic query feature can be used to trace down the cyber-crime records. This feature can also be used to identify some malicious traffic that the IDP/IPS device cannot detect. The IDP/IPS device cannot detect attacks within encrypted traffic, such as HTTP over SSL(HTTPS), the SSH sessions and the virtual private network(VPN) connections. That means you need another method to detect the network traffic. The following graph shows a malicious active that launch by an infected printer in the real world.
It generate 43,658,803 packets / 6.13 GB within 5 minutes. The malicious traffic caused the high CPU usage (99%) on the core-switch and caused the internet connection problems. We believe that it is a good idea to choose "the dynamic traffic query" as your network traffic monitoring tool.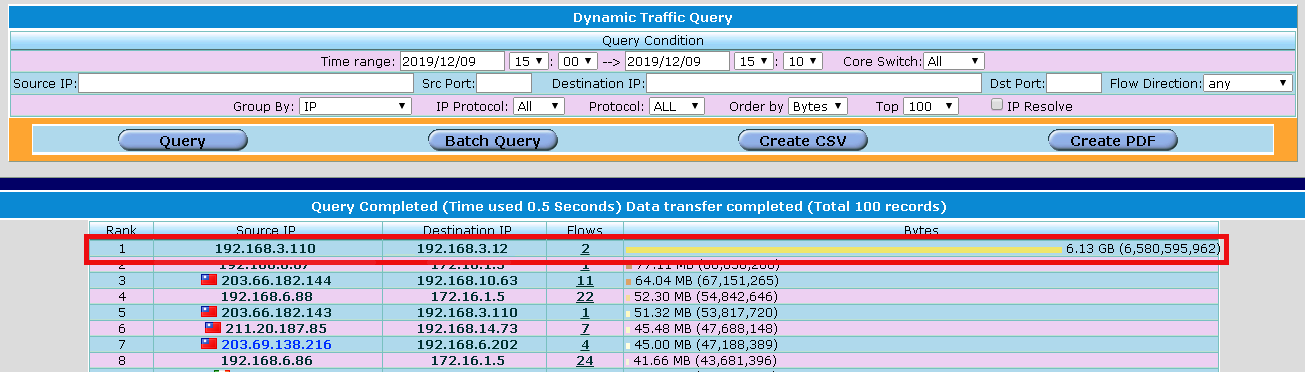
- Provide different kinds of network traffic report;
- Malicious activity protection:
- Port scanning detection
- SSH password-guessing detection
- UDP flooding attack detection
-
For UDP flooding attack, people always think the attack is launched from outside. That is the most common types of cases. The hackers would prefer to relay hack rather than use their network bandwidth. The relay attack will also consume the victims' bandwidth and may cause the network paralysis. The following graph shows that a UDP flooding attack which was launched from inside.
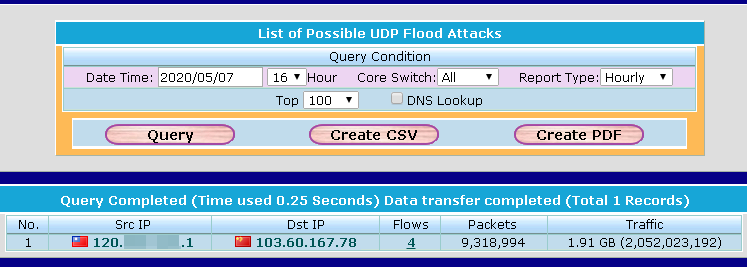
- Denial-of-Service(DoS) attack detection
-
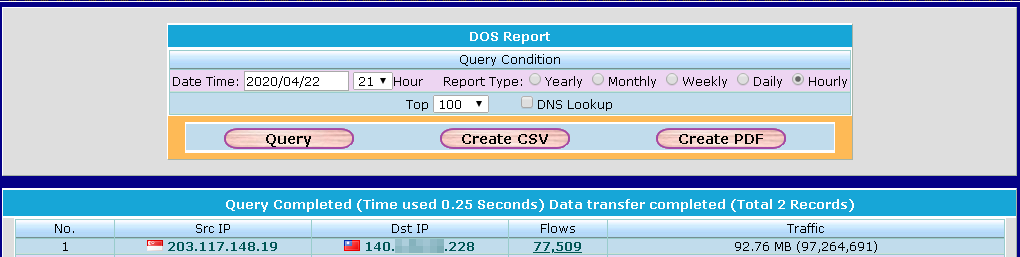
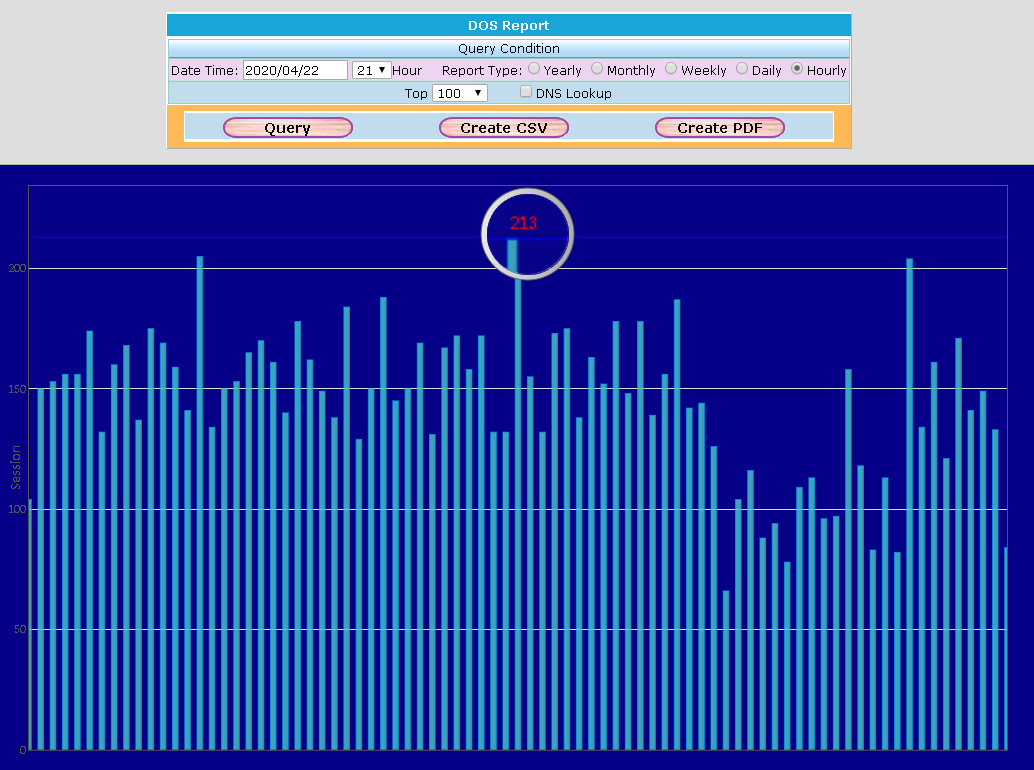
It might get a false negative result if you use the threshold to identify the network traffic is a DoS attack or not. The hackers know the threshold value cannot be set too low so they will use this blind-spot to launch the attack. That means the most of IPS which use the threshold methods for DoS will get the false negative result.The following graph shows that a real DoS attack.
The maximum of flow/second is 213.
- Worm detection (some ransomware spreading like a worm can be detected)